4 Trends in Cybersecurity To Keep Attackers at Bay

Cybersecurity is an ever-evolving field, with new trends coming up constantly: as attackers expose and exploit new vulnerabilities, the industry responds by developing novel techniques and technologies to protect and secure data wherever it may reside.
This dynamic is, unfortunately, the result of unfavorable breach economics – while the average time spent on an attack against typical IT security infrastructure is 70 hours according to Ponemon research, the marginal cost of each attack is near 0.
However, recent trends in cybersecurity, namely homomorphic encryption, moving target defense, quantum encryption and service mesh layers, have started shifting the balance of security from attacker to defender.
Trend #1: Homomorphic encryption

Source: CB Insights - "The Future of Data Security"
Sensitive data exposure is classified by OWASP as the third most critical web application vulnerability. Encryption is the primary solution, but is only available for data at rest and in transit, leaving data in use exposed. For instance, credit card details can be encrypted when stored and transmitted encrypted, but must be decrypted and exposed at the point of processing.
One method of securing data during processing is homomorphic encryption. And this is, without a doubt, one of the top trends in cybersecurity that you can find nowadays. Homomorphic encryption allows operating on encrypted data as if it was unencrypted data. The technique was created in 1978, but proved too computationally intensive and impractical at the time.
The first fully homomorphic encryption system, built by Craig Gentry, was incredibly slow and took 100 trillion times as long to perform calculations of encrypted data than plaintext analysis. Microsoft reported applying the encryption system to deep-learning neural networks and claimed it can make 51,000 predictions per hour with 99% accuracy while studying a stream of encrypted input images. IBM reported in March 2018 it rewrote its C++ homomorphic encryption library and claimed it runs 75 times faster. These advancements have enabled innovative startups to commercialize homomorphic encryption and finally bring the technology to market.
The demand for homomorphic encryption will explode as the volume of data being processed increases due to the rollout of 5G, autonomous vehicles, and AR / VR becoming widespread. Homomorphic encryption solutions are perfect for enabling compliance with various requirements including HIPAA, GDPR, and HITRUST.
This technology can also further enable secure cloud migration for large enterprises, and could be licensed to companies like Dropbox or Box to offer fully encrypted storage while allowing users to search within documents stored on their servers.
Trend #2: Moving Target Defense

In the current IT environment, most systems and networks operate in a relatively static configuration designed in a time when malicious exploitation of system vulnerabilities was not a concern. Addresses, workload names, networks and various configuration parameters remain more or less the same over long periods of time.
This provides attackers with an asymmetric advantage, as adversaries are able to engineer different attacks at a near zero marginal cost. To address this, the Moving Target Defense (MTD) methods and tools dynamically shift the attack surface, making it more difficult for attackers to strike, diminishing the attacker’s advantage.
MTD is the concept of controlling change across multiple system dimensions in order to increase uncertainty and apparent complexity for attackers, reduce their window of opportunity and increase the costs of their probing and attack efforts.
Broadly speaking, there are three types of MTD:
- Network-level – Techniques include IP hopping (changing host IP address), obfuscating port traffic through random assignment of port numbers, and spoofing host information such as OS types and versions
- Host-level – Involves changes to host and OS-level resources, and changes to naming and configurations
- Application-level – Includes address space layout randomization involving randomly arranging memory layout, changes in application types, versioning, and routing through different hosts, and alterations to programming languages used, compiling processes and alteration to the source code itself
MTD represents a complete paradigm shift in security, as it reduces the need for threat detection by constantly shifting the attack surface and guarding against undetected attacks. As an example, take Morphisec’s MTD offering, which works as follows:
- Morph & cloak – As an application loads to the memory space, Morphisec’s polymorphic engine mutates the process structure, and locations of libraries, functions, variables and other data segments are transformed in a controlled manner. Each run is unique, per process instance, making the memory constantly unpredictable to attackers.
- Protect & deceive – Next, legitimate application code is made aware of the new locations of its required resources. The application continues to load normally and runs without any change in its behavior. However, a lightweight dummy of the original application memory is kept to use as a trap.
- Prevent & uncover – Attackers target the original structure, unaware it is a dummy. Lacking knowledge of the new structure, malicious code cannot access the functions it needs and fails to execute, thus stopping the kill chain.
Trend #3: Quantum Encryption
As anyone who has spent time in a classroom knows, some types of math are more difficult than others. For instance, multiplying two prime numbers to find their product is pretty straightforward. But the opposite process, essentially factorizing that product into the original primes without knowing anything about what they are, is extremely hard.
While this process may seem esoteric, it’s in part the foundation of modern encryption technology that secures everything, from credit card information to patient medical records.
Unfortunately, quantum computers will soon render some of our strongest encryption useless, cracking high-entropy keys in seconds, thanks to their ability to quickly work out long prime numbers used to generate them. In fact, the director of IBM Research recently noted that “anyone that wants to make sure that their data is protected for longer than 10 years should move to alternate forms of encryption now.” In response, Quantum Key Distribution (QKD) technologies are being developed and enable secure transmission of data without using traditional public key encryption.
QKD works by having a sender transmit a photon, which is an elementary particle and effectively a minute energy packet of electromagnetic radiation, one at a time to a receiving unit.
At the same time, a quantum property is assigned individually to each photon, such as position or spin, and designates whether that photon represents a one or a zero. Unlike a standard bit, which can either hold a value of one or a zero, a quantum bit, or qubit, can simultaneously represent one and zero.
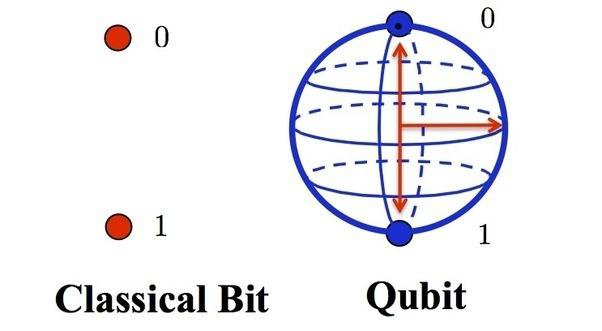
This system is inherently more secure than standard cryptography techniques because if the photon is observed while being transferred, it collapses into a fixed state and the previous superposition fades – the qubit now represents either a one or a zero, just like a classical bit.
What this means is that if a third party intercepts the key transmission and reads it, they won’t be able to re-transmit it to the intended receiver in the same state it was sent in; if they try, the receiver will get meaningless data and it will be apparent someone is tapping the line.
The biggest problem with this trend in cybersecurity is that with current QKD technology only one photon can be sent about 60 miles down a fiber-optic cable before it’s too dim to be received, and the photon needs to be directly transmitted.
Trend #4: Service Mesh Layers
This is the fourth (and last) of the latest trends in cybersecurity that we’ve put together for you in this article.
Over the past few years, microservice-based architectures have been widely adopted due to their support for rapid provisioning, failure tolerance, and their ability to scale microservices without replicating the entire monolith.
However, a microservice-based architecture introduces new challenges, as implementing functionalities related to service-to-service communication such as load balancing from scratch is very time-consuming. Since these inter-service communication requirements are standard across all microservice implementations, offloading these tasks to a different layer would effectively address this issue.
That layer has been realized as a service mesh, which is a configurable infrastructure layer for managing service-to-service communication, and enhances flexibility, reliability, and speed. The service mesh can be understood as a layer of abstraction that sits on top of TCP/IP.
Common features provided by service meshes include:
- Circuit breaking
- Load balancing
- Service discovery
- Control over request routing
- TLS encryption and termination between endpoints and key management
- Simple blacklist and whitelist-based access control
- Metrics on instrumentation at the service-to-service layer
Service mesh layers are being rapidly adopted due to the added security features they provide microservice-based architectures, allowing organizations to limit lateral movement after a breach has occurred. In fact, over the past year, Paypal, Ticketmaster, and Credit Karma have all added a service mesh layer to their applications. The two most popular implementations of service mesh layers are Istio, released in 2017 by Google, IBM and Lyft, and Linkerd.

Source: Istio
While these four cybersecurity technologies are relatively nascent, results have already been promising. For instance, research conducted at George Mason University shows that the moving target defense approach is effective experimentally in certain cases.
Time will tell whether these cybersecurity innovations can keep attackers at bay for long, but the future looks bright.
At Plug and Play's Cybersecurity accelerator we are in touch with corporations and startups that are changing the world as we know it. Join our platform today.



